Get Started in 5 Minutes
A lightning‑fast guide to protect your first endpoint with RLaaS.
1 · Sign In
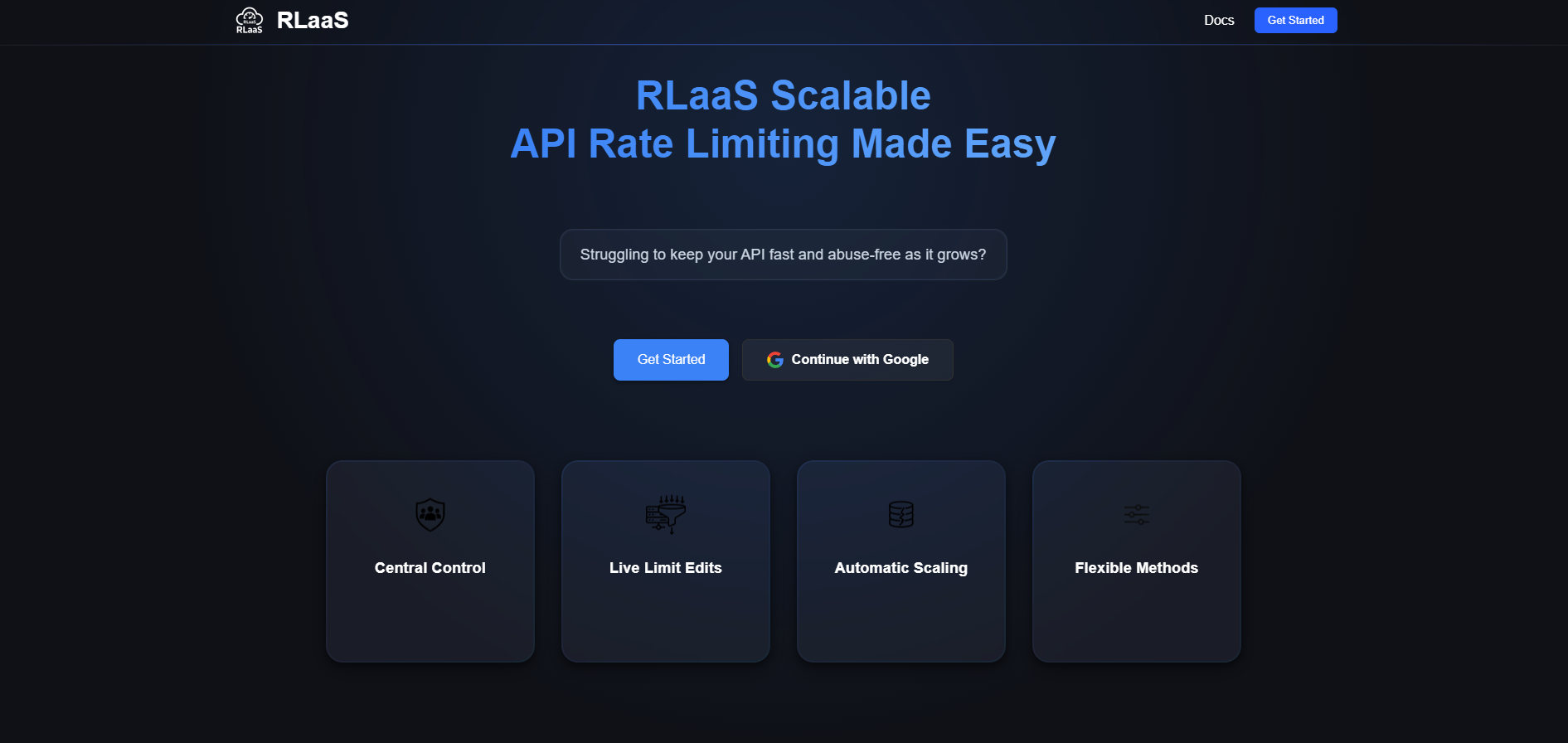
- Open rlaas.tech
- Click Continue with Google – your workspace is created in seconds.
2 · Create a Project & Copy the API Key
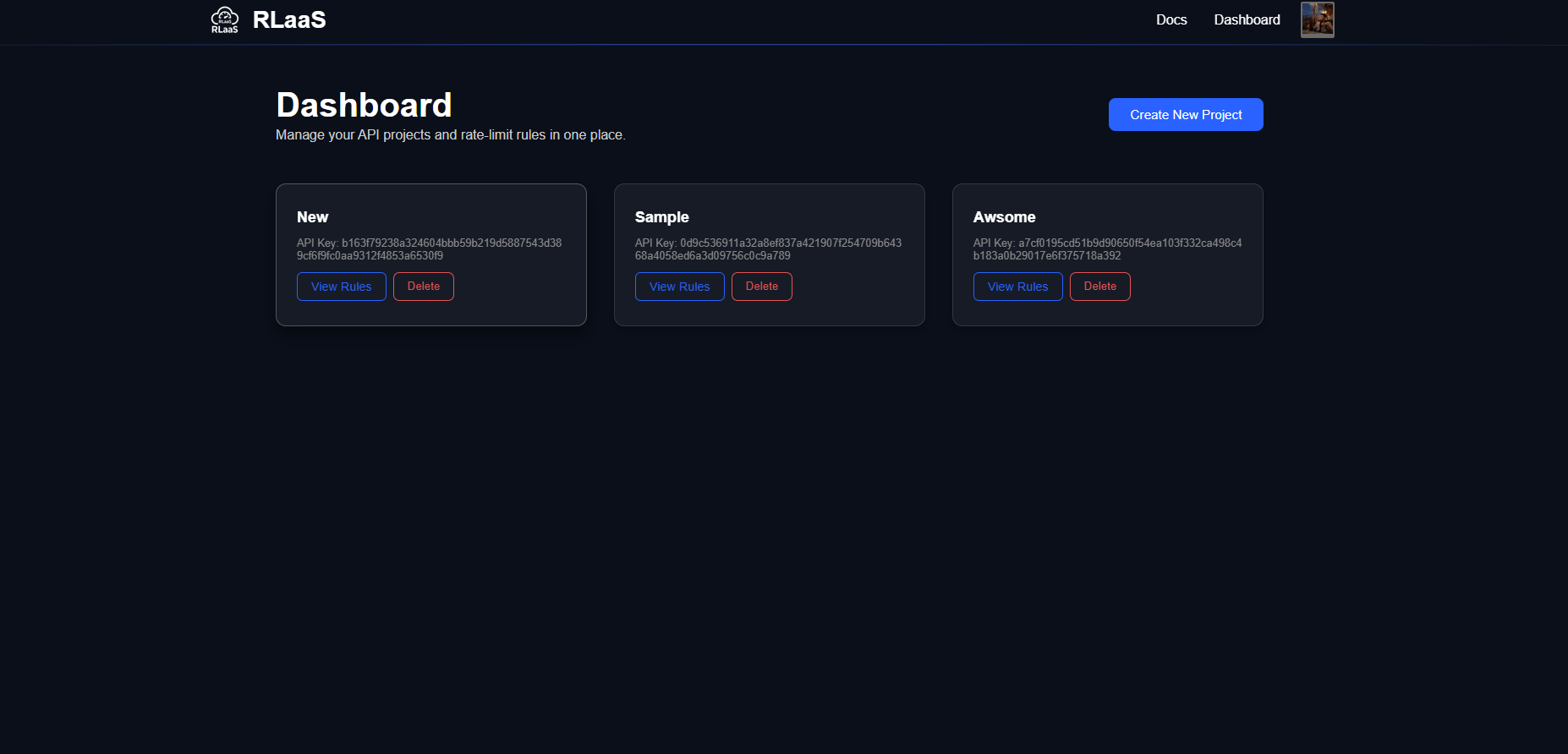
- Dashboard → Create New Project → Name it → Save
- Copy the generated API Key and export it as an env‑var:
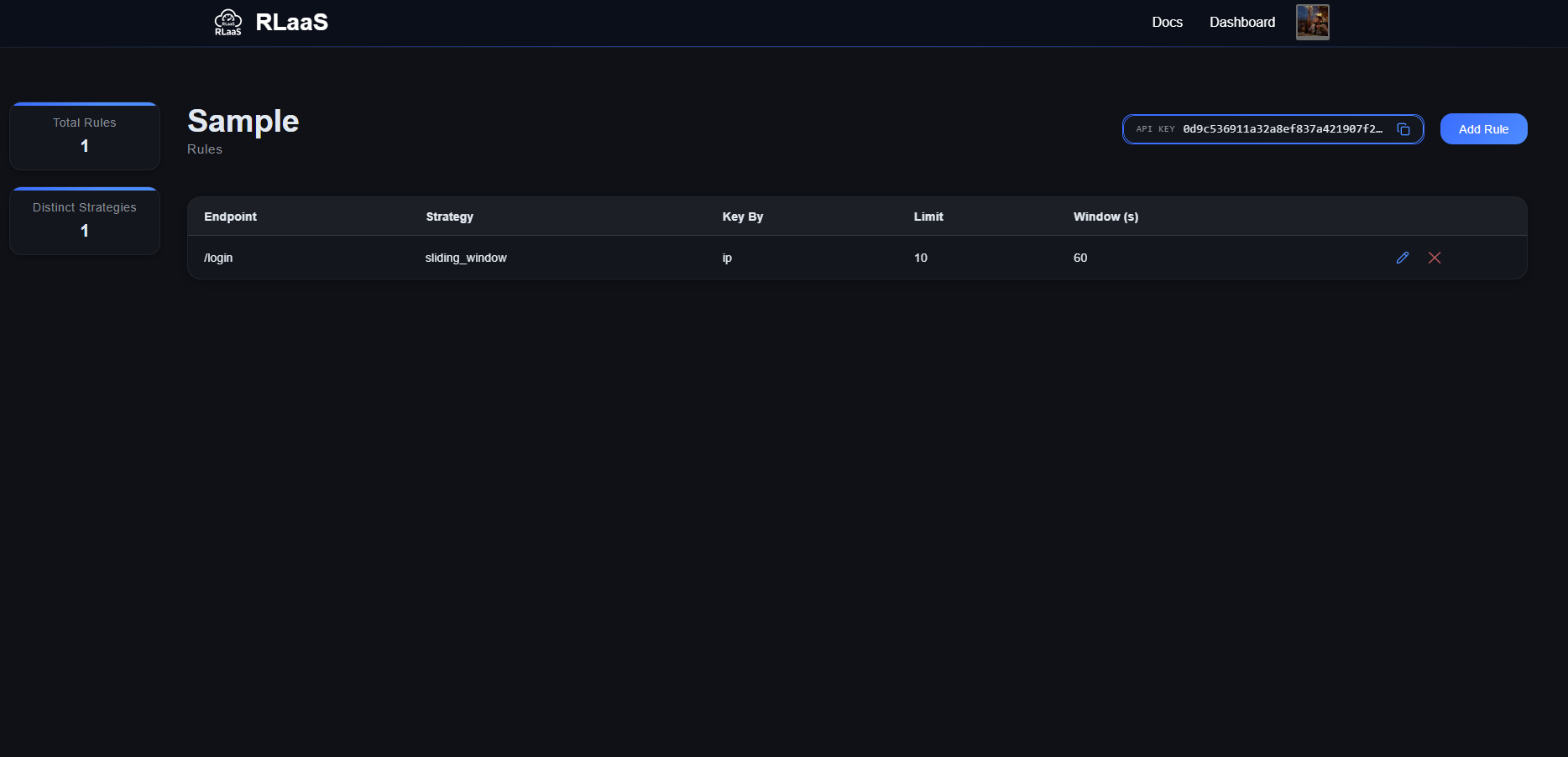
- Click the view rules button and open the rule-management page per project
shell
export RLAAS_API_KEY="<your‑key‑here>"
3 · Add Your First Rule
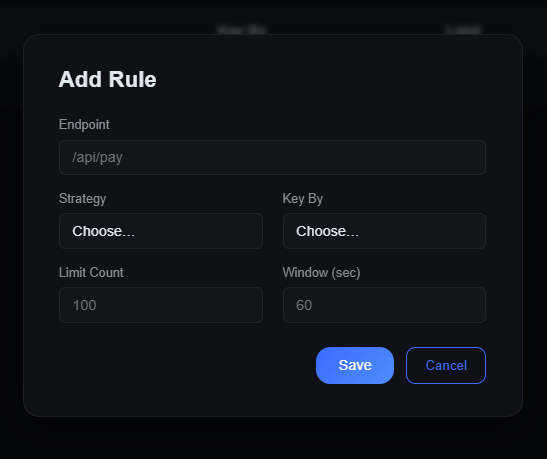
| Field | Example | Description |
|---|---|---|
| Endpoint | /login | Path you want to protect |
| Strategy | sliding | fixed • sliding • token • leaky |
| Key By | ip | ip or api_key |
| Limit | 10 | Max requests allowed |
| Window | 60s | Sliding/fixed window length |
4 · Call the /check Endpoint
- Go
- Java
- Python
- C#
- JavaScript
main.go
// tiny-login-test.go
// Minimal Go test server that rate-limits /login via RLaaS.
package main
import (
"bytes"
"encoding/json"
"io"
"log"
"net"
"net/http"
)
const rlaasURL = "https://api.rlaas.tech/check"
const apiKey = "<YOUR_API_KEY>" // ← paste your key
type payload struct {
APIKey string `json:"api_key"`
Endpoint string `json:"endpoint"`
Key string `json:"key"`
}
func main() {
http.HandleFunc("/login", func(w http.ResponseWriter, r *http.Request) {
// extract remote IP (no proxy handling here)
clientIP, _, _ := net.SplitHostPort(r.RemoteAddr)
// build RLaaS request payload
body, _ := json.Marshal(payload{
APIKey: apiKey,
Endpoint: "/login",
Key: clientIP,
})
// ask RLaaS if this hit is allowed
resp, err := http.Post(rlaasURL, "application/json", bytes.NewReader(body))
if err != nil {
http.Error(w, "RLaaS check failed: "+err.Error(), http.StatusBadGateway)
return
}
defer resp.Body.Close()
// proxy RLaaS response & status code back to caller
w.WriteHeader(resp.StatusCode)
io.Copy(w, resp.Body)
})
log.Println("⇢ http://localhost:8080/login")
log.Fatal(http.ListenAndServe(":8080", nil))
}
Main.java
// Minimal Java HTTP server that uses RLaaS to guard /login.
import com.sun.net.httpserver.*;
import java.io.*;
import java.net.*;
import java.net.http.*;
public class TinyLoginTest {
private static final String RLAAS_URL = "https://api.rlaas.tech/check";
private static final String API_KEY = "<YOUR_API_KEY>";
public static void main(String[] args) throws IOException {
HttpServer server = HttpServer.create(new InetSocketAddress(8080), 0);
server.createContext("/login", exchange -> {
String clientIP = exchange.getRemoteAddress().getAddress().getHostAddress();
String json = String.format(
"{\"api_key\":\"%s\",\"endpoint\":\"/login\",\"key\":\"%s\"}",
API_KEY, clientIP);
HttpRequest req = HttpRequest.newBuilder(URI.create(RLAAS_URL))
.header("Content-Type", "application/json")
.POST(HttpRequest.BodyPublishers.ofString(json))
.build();
HttpResponse<String> res = HttpClient.newHttpClient()
.send(req, HttpResponse.BodyHandlers.ofString());
exchange.sendResponseHeaders(res.statusCode(), res.body().length());
try (OutputStream os = exchange.getResponseBody()) {
os.write(res.body().getBytes());
}
});
server.start();
System.out.println("⇢ http://localhost:8080/login");
}
}
example.py
from flask import Flask, request, Response
import requests, json
RLAAS_URL = "https://api.rlaas.tech/check"
API_KEY = "<YOUR_API_KEY>"
app = Flask(__name__)
@app.post("/login")
def login():
data = {
"api_key": API_KEY,
"endpoint": "/login",
"key": request.remote_addr,
}
res = requests.post(RLAAS_URL, json=data)
return Response(res.content, status=res.status_code, mimetype="application/json")
if __name__ == "__main__":
app.run(port=8080)
Program.cs
// dotnet new web -n TinyLoginTest && replace Program.cs with this.
var builder = WebApplication.CreateBuilder(args);
var app = builder.Build();
const string rlaasUrl = "https://api.rlaas.tech/check";
const string apiKey = "<YOUR_API_KEY>";
app.MapPost("/login", async (HttpContext ctx, HttpClient http) =>
{
var clientIP = ctx.Connection.RemoteIpAddress!.ToString();
var payload = new
{
api_key = apiKey,
endpoint = "/login",
key = clientIP
};
var res = await http.PostAsJsonAsync(rlaasUrl, payload);
ctx.Response.StatusCode = (int)res.StatusCode;
await res.Content.CopyToAsync(ctx.Response.Body);
});
app.Run("http://localhost:8080");
request.js
const express = require("express");
const fetch = require("node-fetch");
const app = express();
const RLAAS_URL = "https://api.rlaas.tech/check";
const API_KEY = "<YOUR_API_KEY>";
app.post("/login", express.json(), async (req, res) => {
const payload = {
api_key: API_KEY,
endpoint: "/login",
key: req.ip,
};
const rl = await fetch(RLAAS_URL, {
method: "POST",
headers: { "Content-Type": "application/json" },
body: JSON.stringify(payload),
});
res.status(rl.status).send(await rl.text());
});
app.listen(8080, () => console.log("⇢ http://localhost:8080/login"));
RLaaS responses are minimal and designed for fast decision-making:
- On success, the server responds with JSON:
{ "allowed": true }- On failure (e.g. limit exceeded), the server returns plain text:
Rate limit exceededNote: You should treat any non-
allowed: trueresponse as a rejection.
This includes checking the status code (e.g. 429) or falling back when the response is not JSON.⚙️ In production, it’s recommended to handle both cases explicitly —
parse and act onallowed: true, and treat everything else as a denial to ensure consistent throttling behavior.